Blockchain security with Blockchain-protected database
Blockchain-Protected Database
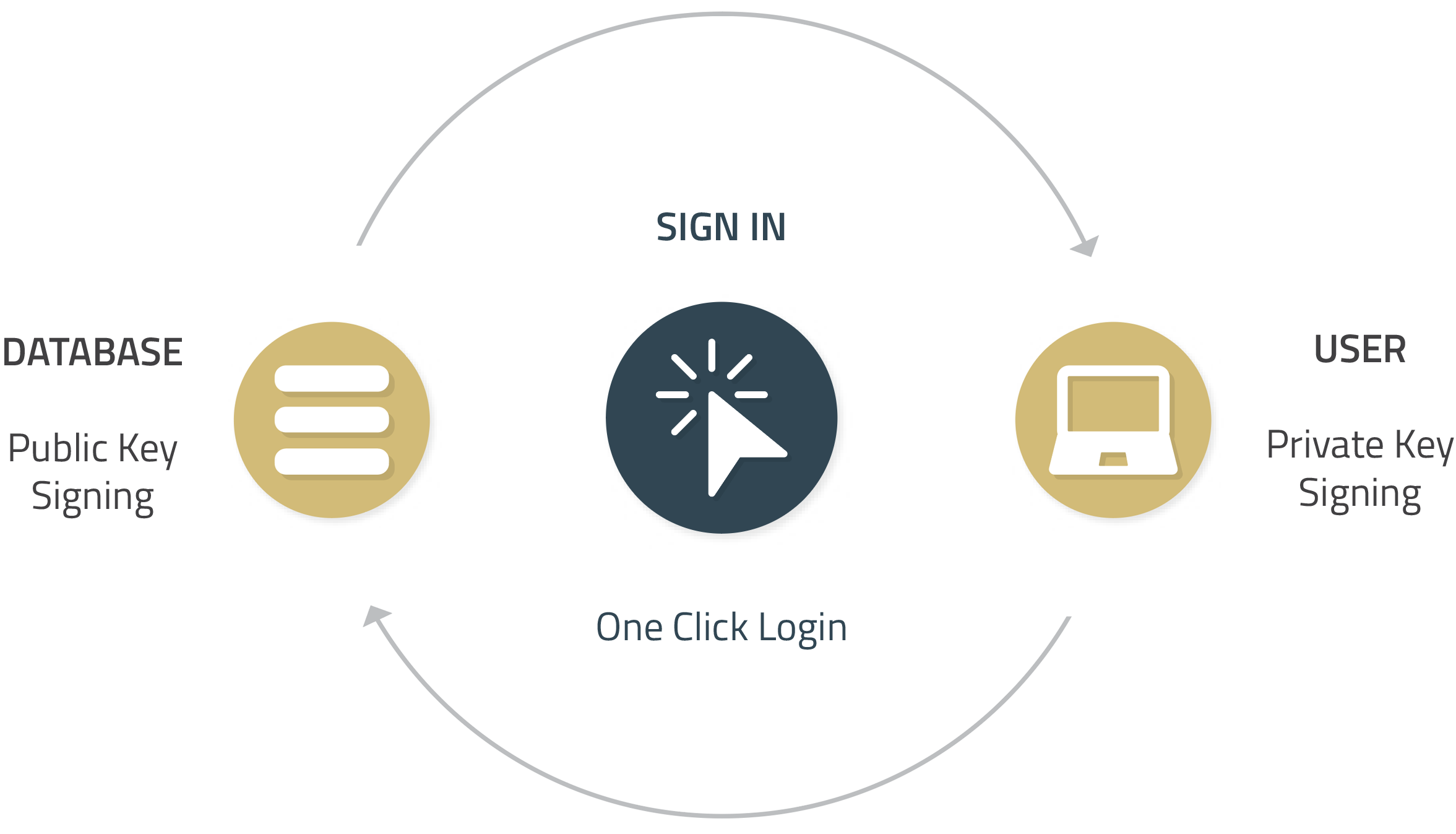
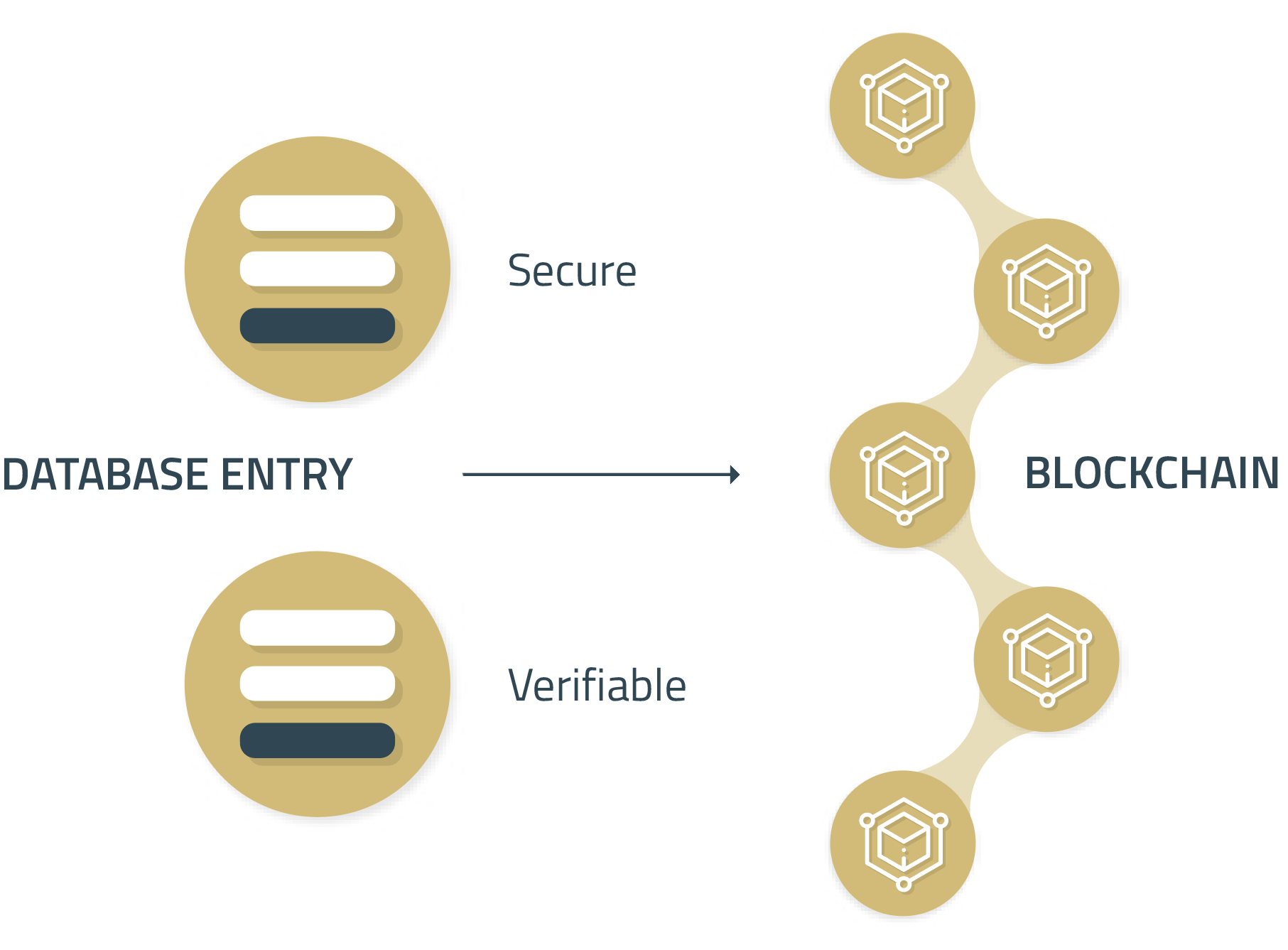
Our software is taking snapshots of your database or recent transactions multiple times a day and creating a cryptographic signature of your private data. By exporting and storing the data on a public blockchain ledger, a database manager can transparently share any information with all of your stakeholders through block explorers, without violating any blockchain security protocols.
This way, any unauthorized change of the past database records would be clearly visible and provable. The software safely stores and secures the data, so any possible changes of the data itself would not produce the same cryptographic signature of the snapshot as originally stored on a blockchain, thus proving that the original data was tempered with.
With the help of our solution, your database managers can now periodically take snapshots of your database and store a cryptographic signature on a public or consortium blockchain, where all of the stakeholders have access and viewing permission to recheck these signatures themselves.
Bd not produce the same cryptographic signature of the snapshot as originally stored on a blockchain.